THE CALIFORNIA AGE-APPROPRIATE DESIGN CODE
Image Credit: Markus Spiske from Unsplash
***Update: On September 15, 2022, Governor Newsom signed AB 2273, establishing the California Age-Appropriate Design Code Act.
Who It Covers, What It Requires & How It Compares to the UK
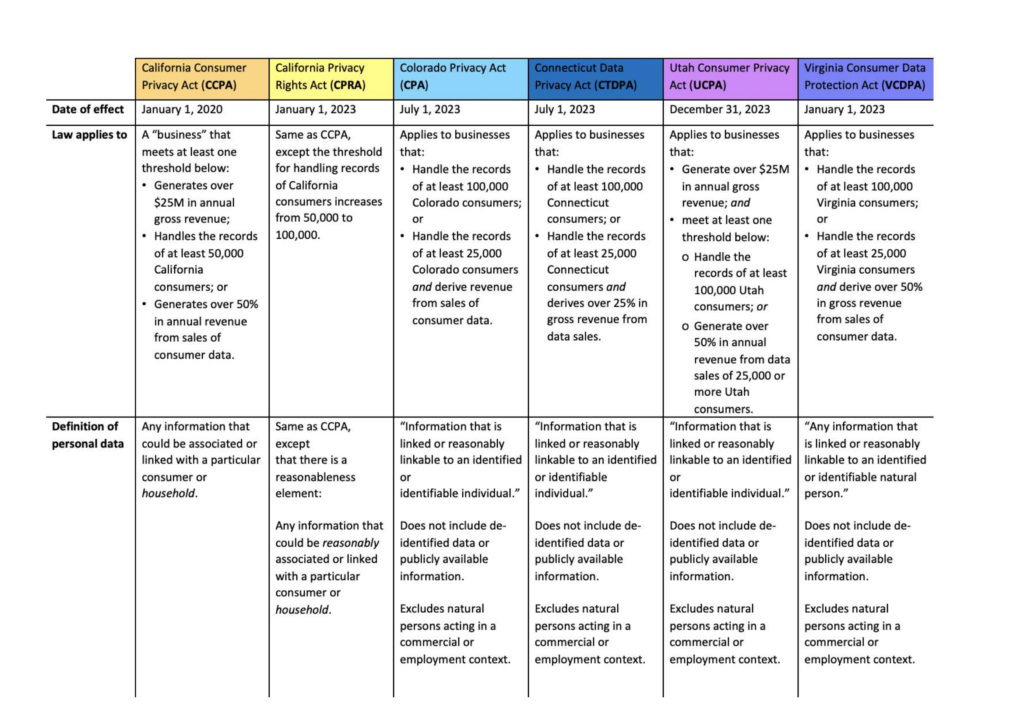
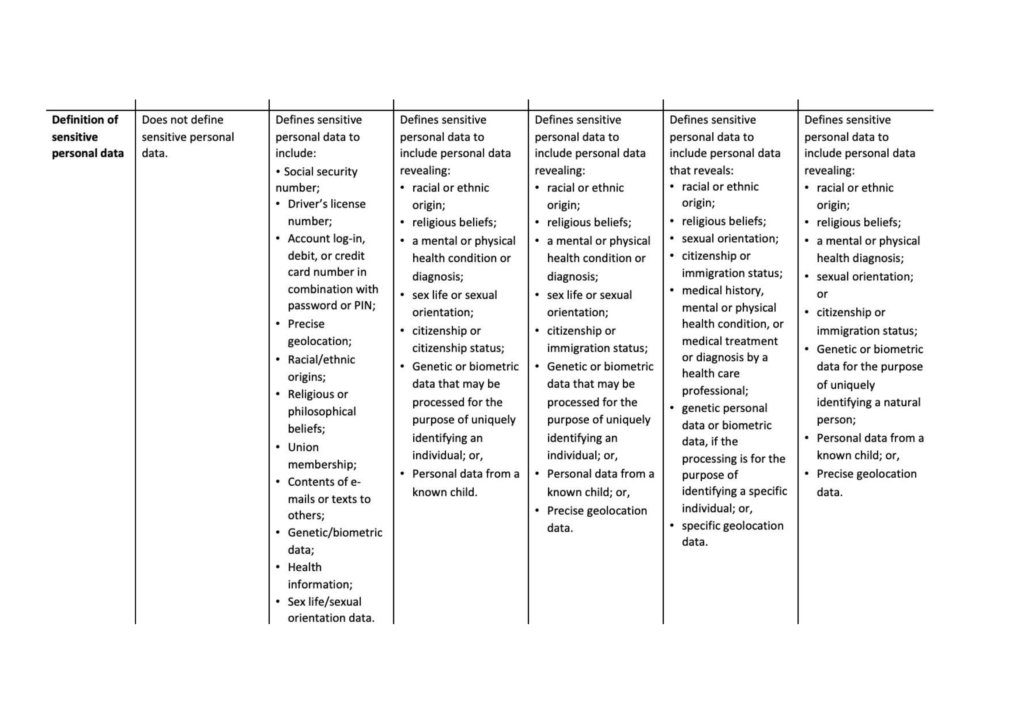
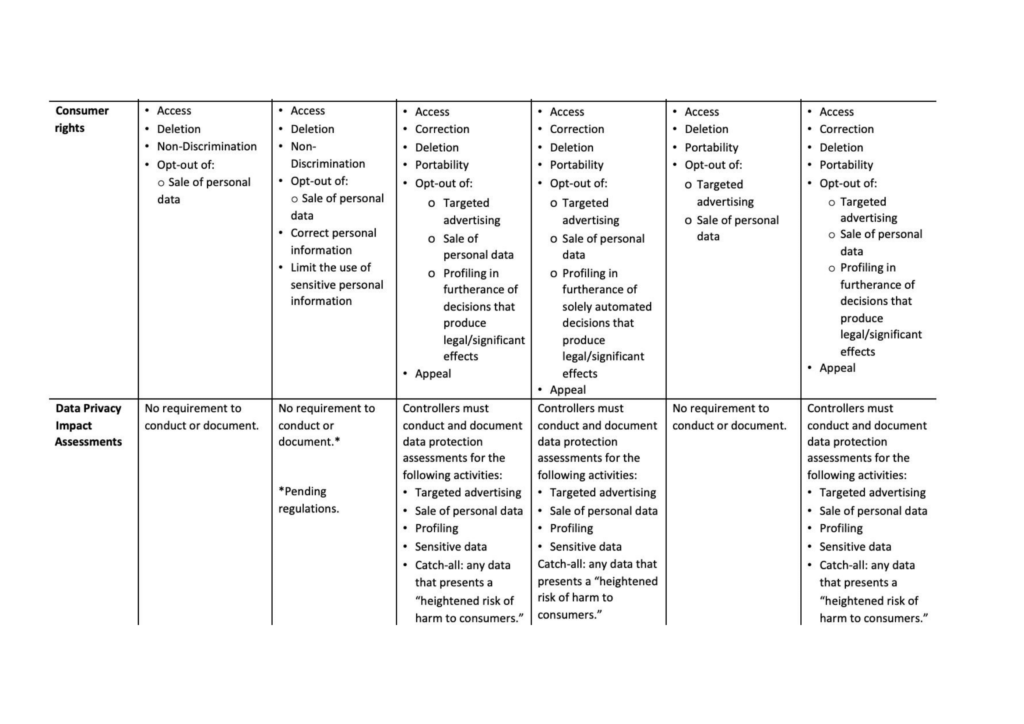
Effective July 1, 2024, the California Age-Appropriate Design Code imposes obligations on businesses[1] that provide an “online service, product, or feature” that is “likely to be accessed by children.”[2] Children are defined as California residents[3] “who are under 18 years of age.”[4] The law provides factors for whether an online service, product, or feature (S/P/F) is “likely to be accessed” by California residents under the age of 18:[5]
- It is directed to children as defined by COPPA.[6]
- It is determined, based on competent and reliable evidence regarding audience composition, to be routinely accessed by a significant number of children, or it is substantially similar to an online S/P/F that meets this factor.
- It displays advertisements marketed to children.
- It has design elements known to be of interest to children, including games, cartoons, music, and celebrities who appeal to children.
- Based on internal research, a significant amount of the audience is children.
An online S/P/F is defined by what it is not, and the definition notably exempts the “delivery or use of a physical product.”[7] This exemption diverts from the UK version of the law, which covers “connected toys and devices.”[8]
Compared to the UK’s Common-Sense Approach
The US version of the law provides no guidance on what it means for a “significant number of children” to “routinely access[]” the online S/P/F. However, the law makes clear in its legislative findings that covered businesses may look to guidance and innovation in response to the UK version when developing US-covered online S/P/F.[9]
ICO states that the term “likely to be accessed by” is purposefully broad, covering “services that children [are] using in reality,” not just those services specifically targeting children.[10] However, ICO recognizes that the term is not so broad as to “cover all services that children could possibly access.”[11] The key difference is whether it is “more probable than not” that an online S/P/F will be accessed by children, and businesses should take a “common sense approach to this question.”[12]
To illustrate this point: